
In an era of rapid development, passing the Cisco 350-401 ENCOR exam is more complex than ever. Prepare for the exam with valid 350-401 ENCOR dumps! You now have to worry about the risk of ineffective dumps, such as outdated, duplicate questions, and incorrect answers.
You can reduce the risk of facing invalid dumps by taking proactive measures.
With the proper 350-401 ENCOR dumps, you can ensure exam success. Pass4itSure 350-401 ENCOR dumps https://www.pass4itsure.com/350-401.html can do it, with 1021 valid questions and answers to help you prepare for the exam easily.
Don’t fall into the trap of free exam questions
There are many dumps of Cisco 350-401 on the market today, some of which are too complex and can cause headaches in the brain.
For example, a well-known website claims to offer free test questions for a wide range of test takers, which does attract people’s attention, but after you review a few questions, you need to purchase them before you can continue to view them.
Can this kind of dishonest behavior in the first place still be trusted?
Don’t believe that high price is good quality
Know that high price does not equal high quality 350-401 ENCOR dumps! The purpose of our learning to pass the exam is to increase our income, not to let our money go to waste. Those 350-401 ENCOR dumps with inflated prices, don’t choose!
The moderate cost-effective dumps are your first choice
Pass4itSure provides you with personalized services with simple and convenient purchase pages, timely updates, the most authentic 350-401 dumps learning materials presented in PDF and VCE formats and diversified choices.
Most importantly, always define the dumps at a moderate price of $45.99, so that the majority of test takers are free from financial pressure.
So the Pass4itSure 350-401 ENCOR dumps can be considered modest cost-effective dumps.
Latest (ENCOR) 350-401 dumps questions and answers
Question 1:
Refer to the exhibit.

An engineer reconfigures the port channel between SW1 and SW2 from an access port to a trunk and immediately notices this error in SW1\’s log:
*Mar 1 09:47:22.245: %PM-4-ERR_DISABLE: bpduguard error detected on Gi0/0, putting Gi0/0 in err-disable state
Which command set resolves this error?
A. SW1(config-if)#interface G0/0 SW1(config-if)#no spanning-tree bpdufilter SW1(config-if)#shut SW1(config-if)#no shut
B. SW1(config-if)#interface G0/0 SW1(config-if)#no spanning-tree bpduguard enable SW1(config-if)#shut SW1(config-if)#no shut
C. SW1(config-if)#interface G0/0 SW1(config-if)#spanning-tree bpduguard enable SW1(config-if)#shut SW1(config-if)#no shut
D. SW1(config-if)#interface G0/1 SW1(config-if)#spanning-tree bpduguard enable SW1(config-if)#shut SW1(config-if)#no shut
Correct Answer: B
Question 2:
Which two entities are Type 1 hypervisors? (Choose two.)
A. Oracle VM VirtualBox
B. Microsoft Hyper-V
C. VMware server
D. VMware ESX
E. Microsoft Virtual PC
Correct Answer: BD
A bare-metal hypervisor (Type 1) is a layer of software we install directly on top of a physical server and its underlying hardware. There is no software or any operating system in between, hence the name bare-metal hypervisor. A Type 1 hypervisor is proven in providing excellent performance and stability since it does not run inside Windows or any other operating system. These are the most common type 1 hypervisor:
+
VMware vSphere with ESX/ESXi
+
KVM (Kernel-Based Virtual Machine)
+
Microsoft Hyper-V
+
Oracle VM
+
Citrix Hypervisor (formerly known as Xen Server)
Reference: https://phoenixnap.com/kb/what-is-hypervisor-type-1-2
Question 3:
Which two components are required for MPLS Layer 3 VPN configuration? (Choose two)
A. Use MP-BGP for customer routes.
B. Use LDP for customer routes.
C. Use a unique RD per customer VRF.
D. Use pseudowire for Layer 2 routes
E. Use OSPF between PE and CE
Correct Answer: AC
Question 4:
Refer to the exhibit.

An engineer has configured an IP SLA for UDP echo\’s. Which command is needed to start the IP SLA to test every 30 seconds and continue until stopped?
A. ip sla schedule 100 life forever
B. ip sla schedule 30 start-time now life forever
C. ip sla schedule 100 start-time now life 30
D. ip sla schedule 100 start-time now life forever
Correct Answer: A
https://www.cisco.com/c/en/us/td/docs/ios/ipsla/command/reference/sla_book/sla_02.html (Optional) Specifies the number of seconds the IP SLAs operations will actively collect information. The default is 3600 (one hour). it has to be D because B references the wrong SLA, and A doesn\’t actually start it
Question 5:
A local router shows an EBGP neighbor in the Active state. Which statement is true about the local router?
A. The local router has an active prefix in the forwarding table from the neighboring router.
B. The local router has BGP passive mode configured for the neighboring router.
C. The local router is attempting to open a TCP session with the neighboring router.
D. The local router is receiving prefixes from the neighboring router and adding them in RIB-IN.
Correct Answer: C
The BGP session may report in the following states 1 Idle: the initial state of a BGP connection. In this state, the BGP speaker is waiting for a BGP start event, generally either the establishment of a TCP connection or the re-establishment of a previous connection.
Once the connection is established, BGP moves to the next state.
2 Connect: In this state, BGP is waiting for the TCP connection to be formed. If the TCP connection completes, BGP will move to the Open Sent stage; if the connection cannot complete, BGP goes to Active 3 Active:
In the Active state, the BGP speaker is attempting to initiate a TCP session with the BGP speaker it wants to peer with.
If this can be done, the BGP state goes to Open Sent state. 4 Open Sent: the BGP speaker is waiting to receive an OPEN message from the remote BGP speaker 5 Open Confirm:
Once the BGP speaker receives the OPEN message and no error is detected, the BGP speaker sends a KEEPALIVE message to the remote BGP speaker 6 Established: All of the neighbor negotiations are complete.
You will see a number, which tells us the number of prefixes the router has received from a neighbor or peer group.
Question 6:
Refer to the exhibit.
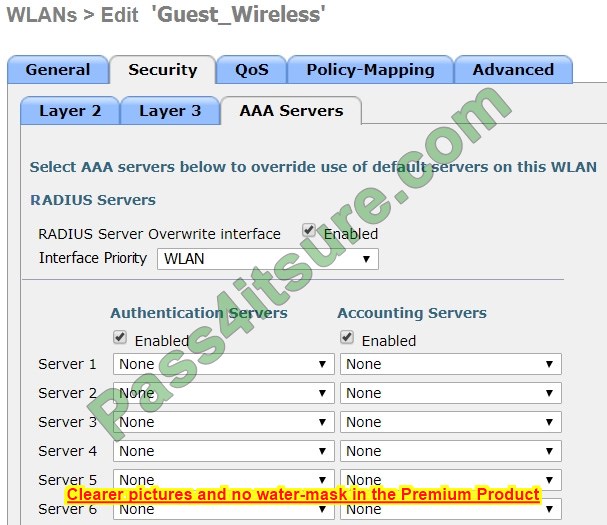
Assuming the WLC\’s interfaces are not in the same subnet as the RADIUS server, which interface would the WLC use as the source for all RADIUS-related traffic?
A. the interface specified on the WLAN configuration
B. any interface configured on the WLC
C. the controller management interface
D. the controller virtual interface
Correct Answer: A
From the guide, the tick box wasn’t checked it would be A. – Check the RADIUS Server Overwrite interface check box to enable the per-WLAN RADIUS source support. When enabled, the controller uses the interface specified on the WLAN configuration as the identity and source for all RADIUS-related traffic on that WLAN
Question 7:
Refer to the exhibit. VPN-A sends point-to-point traffic to VPN-B and receives traffic only from VPN-C VPN-B sends point-to-point traffic to VPN-C and receives traffic only from VPN-A. Which configuration is applied?
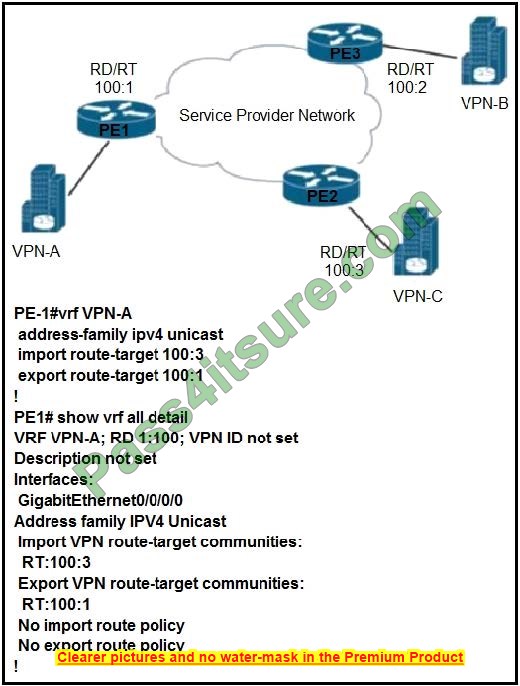
A. PE-2 vrf VPN-B address-family ipv4 unicast import route-target 100:1 export route-target 100:2
B. PE-3 vrf VPN-B address-family ipv4 unicast import route-target 100:1 export route-target 100:2
C. PE-2 vrf VPN-B address-family ipv4 unicast import route-target 100:1 export route-target 100:2
D. PE-3 vrf VPN-B address-family ipv4 unicast import route-target 100:2 export route-target 100:2
Correct Answer: B
Question 8:
A network engineer configures BGP between R1 and R2. Both routers use BGP peer group CORP and are set up to use MD5 authentication. This message is logged to the console of router R1:
`May 5 39:85:55.469: %TCP-6-BADAUTH` Invalid MD5 digest from 10.10.10.1 (29832) to 10.120.10.1 (179) tebleid -0
Which two configurations allow a peering session to form between R1 and R2? (Choose two.)
A. R1(config-router)#neighbor 10.10.10.1 peer-group CORP R1(config-router)#neighbor CORP password cisco
B. R2(config-router)#neighbor 10.120.10.1 peer-group CORP R2(config-router)#neighbor CORP password cisco
C. R2(config-router)#neighbor 10.10.10.1 peer-group CORP R2(config-router)#neighbor PEER password cisco
D. R1(config-router)#neighbor 10.120.10.1 peer-group CORP R1(config-router)#neighbor CORP password cisco
E. R2(config-router)#neighbor 10.10.10.1 peer-group CORP R2(config-router)#neighbor CORP password cisco
Correct Answer: AB
The log is on R1. The question states the console output is from R1, which means that R1 is 10.120.10.1, and R2 is 10.10.10.1. If you missed that you may have assumed the reverse and picked DE.
Question 9:
Which statement about a Cisco APIC controller versus a more traditional SDN controller is true?
A. APIC does support a Southbound REST API
B. APIC supports OpFlex as a Northbound protocol
C. APIC uses a policy agent to translate policies into instructions
D. APIC uses an imperative model
Correct Answer: C
The southbound protocol used by APIC is OpFlex which is pushed by Cisco as the protocol for policy enablement across physical and virtual switches.
Southbound interfaces are implemented with some called Service Abstraction Layer (SAL), which talks to the network elements via SNMP and CLI. Note: Cisco OpFlex is a southbound protocol in a software-defined network (SDN).
Question 10:
Refer to the exhibit.
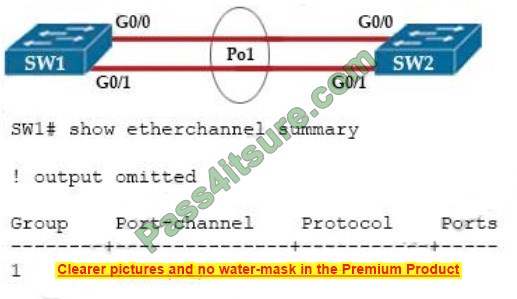
After an engineer configures an EtherChannel between switch SW1 and switch SW2, this error message is logged on switch SW2.
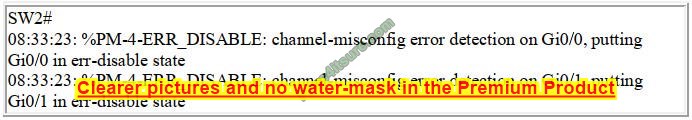
Based on the output from SW1 and the log message received on Switch SW2, what action should the engineer take to resolve this issue?
A. Configure the same protocol on the EtherChannel on switch SW1 and SW2.
B. Connect the configuration error on interface Gi0/1 on switch SW1.
C. Define the correct port members on the EtherChannel on switch SW1.
D. Correct the configuration error on interface Gi0/0 switch SW1.
Correct Answer: A
In this case, we are using your EtherChannel without a negotiation protocol. As a result, if the opposite switch is not also configured for EtherChannel operation on the respective ports, there is a danger of a switching loop.
The EtherChannel Misconfiguration Guard tries to prevent that loop from occurring by disabling all the ports bundled in the EtherChannel.
Question 11:
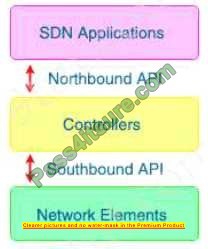
What do Cisco DNA southbound APIs provide?
A. Interface between the controller and the network devices
B. NETCONF API interface for orchestration communication
C. RESful API interface for orchestrator communication
D. Interface between the controller and the consumer
Correct Answer: A
The Southbound API is used to communicate with network devices.
Question 12:
A script contains the statement “while loop != 999:”. Which value terminates the loop?
A. A value less than or equal to 999
B. A value greater than or equal to 999
C. A value not equal to 999
D. A value equal to 999
Correct Answer: D
Question 13:
Based on the router\’s API output in JSON format below, which Python code will display the value of the “hostname” key?
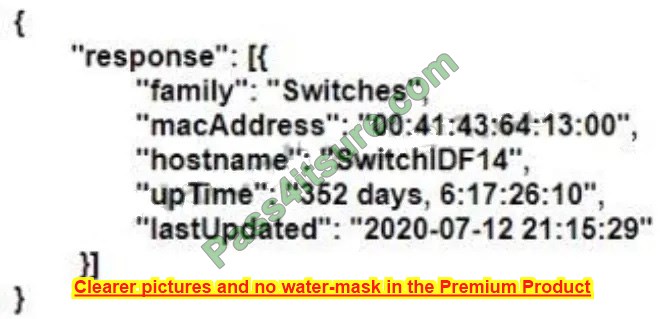
A. json_data = json.loads(response.text) print(json_data[response][0][hostname])
B. json_data = response.json() print(json_data[‘response’][0][‘hostname’])
C. json_data = response.json() print(json_data[‘response’][family][hostname’])
D. json_data = json.loads(response.text) print(json_data[‘response’][‘family’][‘hostname’])
Correct Answer: B
the output was generated from an API get request using the “requests” library. https://www.geeksforgeeks.org/response-json-python-requests/
Question 14:
Which features does Cisco EDR use to provide threat detection and response protection?
A. containment, threat intelligence, and machine learning
B. firewalling and intrusion prevention
C. container-based agents
D. cloud analysis and endpoint firewall controls
Correct Answer: A
Question 15:
You need to implement a First Hop Redundancy Protocol (FHRP) in a dual-stack (IPv4 and IPV6) environment that utilizes devices from multiple different vendors. Which protocol best meets these needs?
A. HSRP
B. GLBP
C. VRRPv1
D. VRRPv2
Correct Answer: D
You have to go with VRRP as the protocol must be vendor agnostic.
Conclusions:
Simply put, the Pass4itSure 350-401 ENCOR dumps are the right choice to ensure validity! You can use it with confidence and prepare for the exam with ease. Get more 350-401 ENCOR dumps questions here.