Studying for Cisco 300-101 dumps Implementing Cisco IP Routing? The Implementing Cisco IP Routing (300-101 ROUTE) exam is a 120 minutes (45-65 questions) assessment in pass4itsure that is associated with the CCNP Routing and Switching, CCDP certification. Take help of new updated Cisco 300-101 dumps pdf practice test software video training guaranteed success online. “Implementing Cisco IP Routing” is the exam name of Pass4itsure Cisco 300-101 dumps test which designed to help candidates prepare for and pass the Cisco 300-101 exam. Because of which, we are very much dutiful and enthusiastic to supporting people to achieve the levels of success by providing Cisco 300-101 preparation dumps that will be great the actual deal Cisco https://www.pass4itsure.com/300-101.html dumps organization certification exams. We offer comprehensive and up-to-date views for Cisco 300-101 certification exams in our PDF files.
[Feb-2018-Cisco 300-101 Dumps Updated From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWWDdYaFM0SVFwMTA
[Feb-2018-Cisco 400-101 Dumps Updated From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWczJDVzl1SUJLWms
Welcome to Pass4itsure Blog: Free Cisco 300-101 Dumps(1-16)
QUESTION 1
A network engineer wants to notify a manager in the events that the IP SLA connection loss threshold reached. Which two feature are need to implements this functionality? (choose two)
A. MOS
B. Threshold action
C. Cisco IOS EEM
D. SNMP traps
E. logging local
300-101 exam Correct Answer: BD
QUESTION 2
In IPv6, the interfaces running OSPF can be configured with multiple address prefixes. Which statement is true about the IPv6 addresses that can be included into the OSPF process?
A. Specific addresses cannot be selected for importation into the OSPF process.
B. Specific addresses can be selected using an ACL.
C. Specific addresses can be selected using a route map.
D. Specific addresses can be selected using a prefix list.
Correct Answer: A
QUESTION 3
Refer to the exhibit.
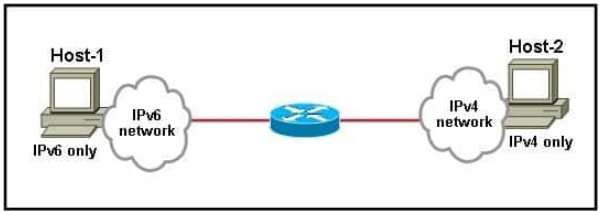
Which interoperability technique implemented on the router would allow Host-1 to communicate with Host-2?
A. Dual Stack
B. NAT-PT
C. 6to4 tunnel
D. GRE tunnel
E. ISATAP tunnel
300-101 dumps Correct Answer: B
QUESTION 4
Which of the following are characteristics of TACACS+? (Choose two.)
A. Uses UDP
B. Encrypts an entire packet
C. Offers robust accounting
D. Cisco-proprietary
Correct Answer: BD
QUESTION 5
The Cisco SA 500 Series Security Appliances are built specifically for businesses with less than 100 employees. What are three important benefits of this device? (Choose three)
A. business-grade firewall
B. premium support via SMART net
C. site-to-site VPN for remote offices
D. Cisco IOS software-based
E. email security
F. XML support
300-101 pdf Correct Answer: ACE
QUESTION 6
Refer to the exhibit.
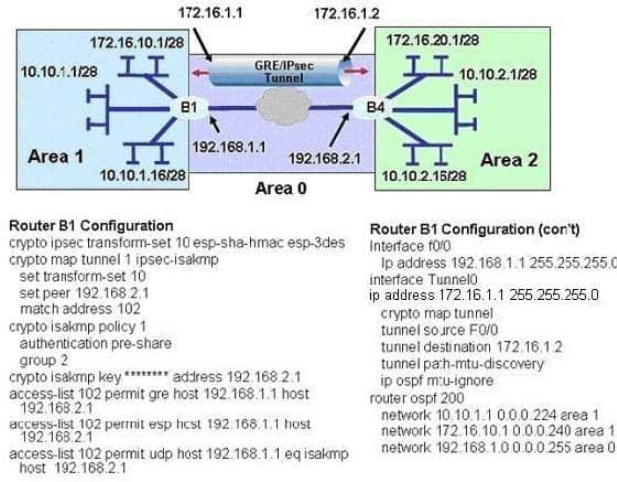
A new TAC engineer came to you for advice. A GRE over IPsec tunnel was configured, but the tunnel is not coming up. What did the TAC engineer configure incorrectly?
A. The crypto isakmp configuration is not correct.
B. The crypto map configuration is not correct.
C. The network 172.16.1.0 is not included in the OSPF process.
D. The interface tunnel configuration is not correct.
Correct Answer: D
QUESTION 7
Which statement describes what this command accomplishes when inside and outside interfaces are correctly identified for NAT? ip nat inside source static tcp 192.168.1.50 80 209.165.201.1 8080 extendable
A. It allows host 192.168.1.50 to access external websites using TCP port 8080.
B. It allows external clients coming from public IP 209.165.201.1 to connect to a web server at 192.168.1.50.
C. It allows external clients to connect to a web server hosted on 192.168.1.50.
D. It represents an incorrect NAT configuration because it uses standard TCP ports.
300-101 vce Correct Answer: C
QUESTION 8
The terrorist organizations are increasingly blocking all traffic from North America or from Internet Protocol addresses that point to users who rely on the English Language. Hackers sometimes set a number of criteria for accessing their website. This information is shared among the co-hackers. For example if you are using a machine with the Linux Operating System and the Netscape browser then you will have access to their website in a convert way. When federal investigators using PCs
running windows and using Internet Explorer visited the hacker’s shared site, the hacker’s system immediately mounted a distributed denial-of-service attack against the federal system. Companies today are engaging in tracking competitor’s through reverse IP address lookup sites like whois.com, which provide an IP address’s domain. When the competitor visits the companies website they are directed to a products page without discount and prices are marked higher for their product. When normal users visit the website they are directed to a page with full-blown product details along with attractive discounts. This is based on IP-based blocking, where certain addresses are barred from accessing a site. What is this masking technique called?
A. Website Cloaking
B. Website Filtering
C. IP Access Blockade
D. Mirrored WebSite
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
Website Cloaking travels under a variety of alias including Stealth, Stealth scripts, IP delivery, Food Script, and Phantom page technology. It’s hot- due to its ability to manipulate those elusive top-ranking results from spider search engines.
QUESTION 9
Bill has started to notice some slowness on his network when trying to update his company’s website while trying to access the website from the Internet. Bill asks the help desk manager if he has received any calls about slowness from the end users, but the help desk manager says that he has not. Bill receives a number of calls from customers that can’t access the company website and can’t purchase anything online. Bill logs on to a couple of this routers and notices that the logs shows network traffic is at all time high. He also notices that almost all the traffic is originating from a specific address. Bill decides to use Geotrace to find out where the suspect IP is originates from. The Geotrace utility runs a traceroute and finds that IP is coming from Panama. Bill knows that none of his customers are in Panama so he immediately thinks that his company is under a Denial of Service attack. Now Bill needs to find out more about the originating IP Address. What Internet registry should Bill look in to find the IP Address?
A. LACNIC
B. ARIN
C. RIPELACNIC
D. APNIC
300-101 exam Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
LACNIC is the Latin American and Caribbean Internet Addresses Registry that administers IP addresses, autonomous system numbers, reverse DNS, and other network resources for that region.
QUESTION 10
System Administrators sometimes post questions to newsgroups when they run into technical challenges. As an ethical hacker, you could use the information in newsgroup posting to glean insight into the makeup of a target network. How would you search for these posting using Google search?
A. Search in Google using the key strings “the target company” and “newsgroups”
B. Search for the target company name at
C. Use NNTP websites to search for these postings
D. Search in Google using the key search strings “the target company” and “forums”
Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
Using is the easiest way to access various newsgroups today. Before http://groups.google.com you had to use special NNTP clients or subscribe to some nntp to web services.
QUESTION 11
Which of the following activities would not be considered passive footprinting?
A. Search on financial site such as Yahoo Financial
B. Perform multiple queries through a search engine
C. Scan the range of IP address found in their DNS database
D. Go through the rubbish to find out any information that might have been discarded
300-101 dumps Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
Passive footprinting is a method in which the attacker never makes contact with the target. Scanning the targets IP addresses can be logged at the target and therefore contact has been made.
QUESTION 12
You are footprinting the www.xsecurity.com domain using the Google Search Engine. You would like to determine what sites link to www.xsecurity .com at the first level of revelance. Which of the following operator in Google search will you use to achieve this?
A. Link: www.xsecurity.com
B. serch?l:www.xsecurity.com
C. level1.www.security.com
D. pagerank:www.xsecurity.com
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
The query [link:] will list webpages that have links to the specified webpage. For instance, [link:www.google.com] will list webpages that have links pointing to the Google homepage. Note there can be no space between the “link:” and the web page url.
QUESTION 13
Doug is conducting a port scan of a target network. He knows that his client target network has a web server and that there is a mail server also which is up and running. Doug has been sweeping the network but has not been able to elicit any response from the remote target. Which of the following could be the most likely cause behind this lack of response? Select 4.
A. UDP is filtered by a gateway
B. The packet TTL value is too low and cannot reach the target
C. The host might be down
D. The destination network might be down
E. The TCP windows size does not match
F. ICMP is filtered by a gateway
300-101 pdf Correct Answer: ABCF
Explanation
Explanation/Reference:
Explanation:
If the destination host or the destination network is down there is no way to get an answer and if TTL (Time To Live) is set too low the UDP packets will “die” before reaching the host because of too many hops between the scanning computer and the target. The TCP receive window size is the amount of received data (in bytes) that can be buffered during a connection. The sending host can send only that amount of data before it must wait for an acknowledgment and window update from the receiving host and ICMP is mainly used for echo requests and not in port scans.
QUESTION 14
Exhibit
Joe Hacker runs the hping2 hacking tool to predict the target host’s sequence numbers in one of the hacking session. What does the first and second column mean? Select two.
A. The first column reports the sequence number
B. The second column reports the difference between the current and last sequence number
C. The second column reports the next sequence number
D. The first column reports the difference between current and last sequence number
Correct Answer: AB
Explanation
Explanation/Reference:
QUESTION 15
While performing a ping sweep of a subnet you receive an ICMP reply of Code 3/Type 13 for all the pings sent out. What is the most likely cause behind this response?
A. The firewall is dropping the packets.
B. An in-line IDS is dropping the packets.
C. A router is blocking ICMP.
D. The host does not respond to ICMP packets.
300-101 vce Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
Type 3 message = Destination Unreachable [RFC792], Code 13 (cause) = Communication Administratively Prohibited [RFC1812]
QUESTION 16
The following excerpt is taken from a honeyput log. The log captures activities across three days. There are several intrusion attempts; however, a few are successful. Study the log given below and answer the following question: (Note: The objective of this questions is to test whether the student has learnt about passive OS fingerprinting (which should tell them the OS from log captures): can they tell a SQL injection attack signature; can they infer if a user ID has been created by an attacker and whether they can read plain source destination entries from log entries.) What can you infer from the above log?
A. The system is a windows system which is being scanned unsuccessfully.
B. The system is a web application server compromised through SQL injection.
C. The system has been compromised and backdoored by the attacker.
D. The actual IP of the successful attacker is 24.9.255.53.
Correct Answer: A
Explanation
Explanation/Reference:

See What Our Customers Are Saying:
We at Pass4itsure are committed to our customer’s success. There are 50,000+ customers who used this preparation material for the preparation of various certification exams and this number of customers is enough for new candidates to trust in these products. Our Cisco 300-101 dumps are created with utmost care and professionalism. We utilize the experience and knowledge of a team of industry professionals from leading organizations all over the world.
We are aware that how important these Cisco 300-101 dumps benefits are to your career, to your future and your job. “Implementing Cisco IP Switched Networks”, also known as 300-101 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 300-101 dumps exam questions answers are updated (570 Q&As) are verified by experts. The associated certifications of 300-101 dumps is CCNP Routing and Switching,CCDP. Just because we also know how traumatic your schedule is, Our Cisco https://www.pass4itsure.com/300-101.html dumps assessment preparing product comes in PDF so you can have the availability on just about every electronic device you own such as the PC, notebooks, Android working system, when on earth and anyplace you want them.
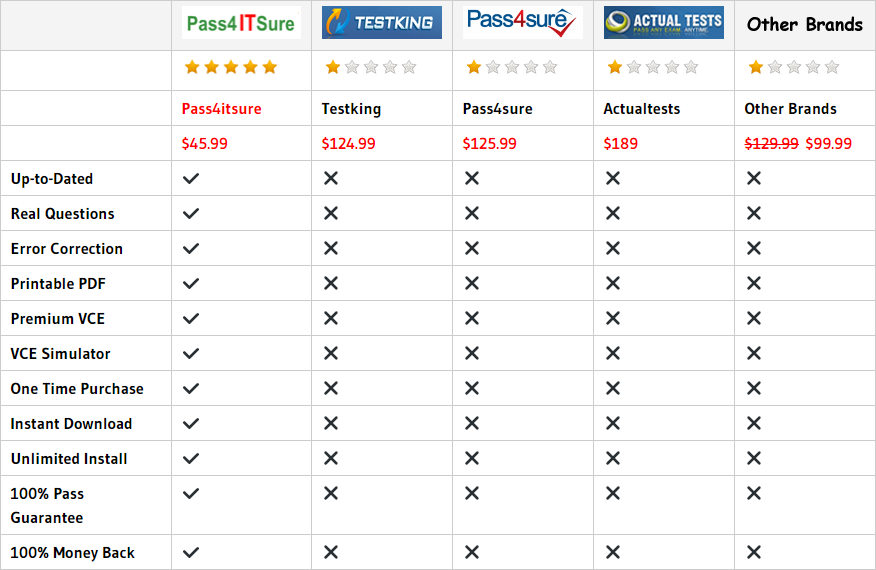
Compared with other brands, Pass4itsure has up to dated exam information, affordable price, instant exam PDF files downloaded, error correction, unlimited install,etc. Such as Pass4itsure New Updated Cisco 300-101 Dumps PDF, Real Cisco 300-101 Dumps PDF Guaranteed Success, We Help You Pass Implementing Cisco IP Routing. Simple and Easy! To take advantage of the guarantee, simply contact Customer Support, requesting the exam you would like to claim. Pass4itsure guarantee insures your success otherwise get your MONEYBACK!