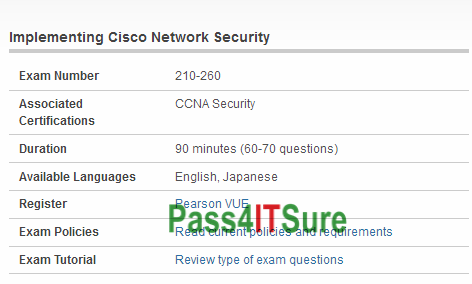
For those that passed the Cisco 210-260 dumps exam what was the format? The Implementing Cisco Network Security (210-260 IINS) exam is a 90 minutes (60-70 questions) assessment in pass4itsure that is associated with the CCNA Security certification. Get 2018 latest Cisco 210-260 dumps IINS exam Implementing Cisco Network Security. “Implementing Cisco Network Security” is the exam name of Pass4itsure Cisco 210-260 dumps test which designed to help candidates prepare for and pass the Cisco 210-260 exam. But the effective implementation of Cisco Network Security exam preparation and understanding of all the basics of Cisco 210–260 are definitely required to pass this critical review of Cisco Deployment of Cisco Network Security.Pass4itsure is a global https://www.pass4itsure.com/210-260.html dumps Cisco Certified Network Associate Security practice exam supplier.
[Jan-2018-Cisco 210-260 Dumps Updated From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWU0xad3NvRWR4Qzg
[Jan-2018-Cisco 210-451 Dumps Updated From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWeFJLMDBQaDMyM1E
Welcome to Pass4itsures Blog: Free Cisco 210-260 Dumps(1-30)
QUESTION 1
How can FirePOWER block malicious email attachments?
A. It forwards email requests to an external signature engine.
B. It scans inbound email messages for known bad URLs.
C. It sends the traffic through a file policy.
D. It sends an alert to the administrator to verify suspicious email messages.
210-260 exam Correct Answer: C
QUESTION 2
What is the actual IOS privilege level of User Exec mode?
A. 1
B. 0
C. 5
D. 15
Correct Answer: A
QUESTION 3
How does PEAP protect the EAP exchange?
A. It encrypts the exchange using the server certificate.
B. It encrypts the exchange using the client certificate.
C. It validates the server-supplied certificate, and then encrypts the exchange using the client certificate.
D. It validates the client-supplied certificate, and then encrypts the exchange using the server certificate.
210-260 dumps Correct Answer: A
QUESTION 4
Refer to the exhibit.
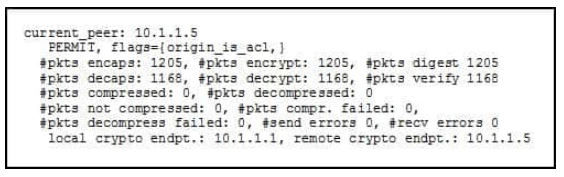
While troubleshooting site-to-site VPN, you issued the show crypto ipsec sa command. What does the given output show?
A. IPSec Phase 2 is established between 10.1.1.1 and 10.1.1.5.
B. ISAKMP security associations are established between 10.1.1.5 and 10.1.1.1.
C. IKE version 2 security associations are established between 10.1.1.1 and 10.1.1.5.
D. IPSec Phase 2 is down due to a mismatch between encrypted and decrypted packets.
Correct Answer: A
QUESTION 5
Which statements about reflexive access lists are true? (Choose three.)
A. Reflexive access lists create a permanent ACE
B. Reflexive access lists approximate session filtering using the established keyword
C. Reflexive access lists can be attached to standard named IP ACLs
D. Reflexive access lists support UDP sessions
E. Reflexive access lists can be attached to extended named IP ACLs F. Reflexive access lists support TCP sessions
210-260 pdf Correct Answer: DEF
QUESTION 6
Which of the following pairs of statements is true in terms of configuring MD authentication?
A. Interface statements (OSPF, EIGRP) must be configured; use of key chain in OSPF
B. Router process (OSPF, EIGRP) must be configured; key chain in EIGRP
C. Router process (only for OSPF) must be configured; key chain in EIGRP
D. Router process (only for OSPF) must be configured; key chain in OSPF
Correct Answer: C
QUESTION 7
What do you use when you have a network object or group and want to use an IP address?
A. Static NAT
B. Dynamic NAT
C. identity NAT
D. Static PAT
210-260 vce Correct Answer: B
QUESTION 8
When a switch has multiple links connected to a downstream switch, what is the first step that STP takes to prevent loops?
A. STP elects the root bridge
B. STP selects the root port
C. STP selects the designated port
D. STP blocks one of the ports
Correct Answer: A
QUESTION 9
In which two situations should you use out-of-band management? (Choose two.)
A. when a network device fails to forward packets
B. when you require ROMMON access
C. when management applications need concurrent access to the device
D. when you require administrator access from multiple locations
E. when the control plane fails to respond
210-260 exam Correct Answer: AB
QUESTION 10
Refer to the exhibit.
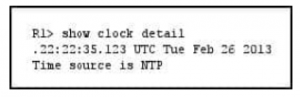
Which statement about the device time is true?
A. The time is authoritative, but the NTP process has lost contact with its servers.
B. The time is authoritative because the clock is in sync.
C. The clock is out of sync.
D. NTP is configured incorrectly.
E. The time is not authoritative.
Correct Answer: A
QUESTION 11
Which type of encryption technology has the broadcast platform support?
A. Middleware
B. Hardware
C. Software
D. File-level
210-260 dumps Correct Answer: C
QUESTION 12
What are the three layers of a hierarchical network design? (Choose three.)
A. access
B. core
C. distribution
D. user
E. server
F. Internet
Correct Answer: ABC
QUESTION 13
Which EAP method uses Protected Access Credentials?
A. EAP-FAST
B. EAP-TLS
C. EAP-PEAP
D. EAP-GTC
210-260 pdf Correct Answer: A
QUESTION 14
Refer to the exhibit.
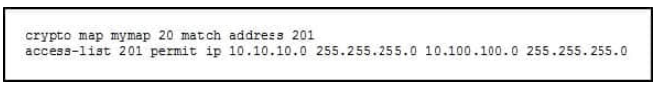
What is the effect of the given command sequence?
A. It defines IPSec policy for traffic sourced from 10.10.10.0/24 with a destination of 10.100.100.0/24.
B. It defines IPSec policy for traffic sourced from 10.100.100.0/24 with a destination of 10.10.10.0/24.
C. It defines IKE policy for traffic sourced from 10.10.10.0/24 with a destination of 10.100.100.0/24.
D. It defines IKE policy for traffic sourced from 10.100.100.0/24 with a destination of 10.10.10.0/24.
Correct Answer: A
QUESTION 15
What is the best way to confirm that AAA authentication is working properly?
A. Use the test aaa command.
B. Ping the NAS to confirm connectivity.
C. Use the Cisco-recommended configuration for AAA authentication.
D. Log into and out of the router, and then check the NAS authentication log.
210-260 vce Correct Answer: A
QUESTION 16
How to verify that TACACS+ connectivity to a device?
A. You successfully log in to the device by using the local credentials.
B. You connect to the device using SSH and receive the login prompt.
C. You successfully log in to the device by using ACS credentials.
D. You connect via console port and receive the login prompt.
Correct Answer: B
QUESTION 17
What is the effect of the ASA command crypto isakmp nat-traversal?
A. It opens port 4500 only on the outside interface.
B. It opens port 500 only on the inside interface.
C. It opens port 500 only on the outside interface.
D. It opens port 4500 on all interfaces that are IPSec enabled.
210-260 exam Correct Answer: D
QUESTION 18
What port option in a PVLAN that can communicate with every other ports
Correct Answer: promiscous
QUESTION 19
What port option in a PVLAN that can communicate with every other ports…
A. promiscous
210-260 dumps Correct Answer: A
QUESTION 20
You want to allow all of your company\’s users to access the Internet without allowing other Web servers to collect the IP addresses of individual users. What two solutions can you use? (Choose two).
A. Configure a proxy server to hide users\’ local IP addresses.
B. Assign unique IP addresses to all users.
C. Assign the same IP address to all users.
D. Install a Web content filter to hide users\’ local IP addresses.
E. Configure a firewall to use Port Address Translation.
Correct Answer: AE
QUESTION 21
Which statement about application blocking is true?
A. It blocks access to specific programs.
B. It blocks access to files with specific extensions.
C. It blocks access to specific network addresses.
D. It blocks access to specific network services.
210-260 pdf Correct Answer: A
QUESTION 22
Which filter uses in Web reputation to prevent from Web Based Attacks? (Choose two)
A. outbreak filter
B. buffer overflow filter
C. bayesian overflow filter
D. web reputation
E. exploit filtering
Correct Answer: AD
QUESTION 23
Which firewall configuration must you perform to allow traffic to flow in both directions between two zones?
A. You must configure two zone pairs, one for each direction.
B. You can configure a single zone pair that allows bidirectional traffic flows for any zone.
C. You can configure a single zone pair that allows bidirectional traffic flows for any zone except the self zone.
D. You can configure a single zone pair that allows bidirectional traffic flows only if the source zone is the less secure zone.
210-260 vce Correct Answer: A
QUESTION 24
which port should (or would) be open if VPN NAT-T was enabled
A. port 500
B. port 500 outside interface
C. port 4500 outside interface
D. port 4500 ipsec
Correct Answer: D
QUESTION 25
What is an advantage of implementing a Trusted Platform Module for disk encryption?
A. It provides hardware authentication.
B. It allows the hard disk to be transferred to another device without requiring re- encryption.dis
C. It supports a more complex encryption algorithm than other disk-encryption technologies.
D. It can protect against single points of failure.
210-260 exam Correct Answer: A
QUESTION 26
What is the transition order of STP states on a Layer 2 switch interface?
A. listening, learning, blocking, forwarding, disabled
B. listening, blocking, learning, forwarding, disabled
C. blocking, listening, learning, forwarding, disabled
D. forwarding, listening, learning, blocking, disabled
Correct Answer: C
QUESTION 27
In which three cases does the ASA firewall permit inbound HTTP GET requests during normal operations? (Choose three).
A. when matching NAT entries are configured
B. when matching ACL entries are configured
C. when the firewall receives a SYN-ACK packet
D. when the firewall receives a SYN packet
E. when the firewall requires HTTP inspection
F. when the firewall requires strict HTTP inspection
210-260 dumps Correct Answer: ABD
QUESTION 28
What feature defines a campus area network?
A. It has a single geographic location.
B. It has limited or restricted Internet access.
C. It has a limited number of segments.
D. it lacks external connectivity.
Correct Answer: A
QUESTION 29
What is a potential drawback to leaving VLAN 1 as the native VLAN?
A. It may be susceptible to a VLAN hoping attack.
B. Gratuitous ARPs might be able to conduct a man-in-the-middle attack.
C. The CAM might be overloaded, effectively turning the switch into a hub.
D. VLAN 1 might be vulnerable to IP address spoofing.
210-260 pdf Correct Answer: A
QUESTION 30
Which three ESP fields can be encrypted during transmission? (Choose three.)
A. Security Parameter Index
B. Sequence Number
C. MAC Address
D. Padding
E. Pad Length
F. Next Header
Correct Answer: DEF

See What Our Customers Are Saying:
We at Pass4itsure are committed to our customer’s success. There are 50,000+ customers who used this preparation material for the preparation of various certification exams and this number of customers is enough for new candidates to trust in these products. Our products are created with utmost care and professionalism. We utilize the experience and knowledge of a team of industry professionals from leading organizations all over the world.
That has most correct Practice materials that enable you to pass the 210–260 dumps exam on the 1st try.Pass4itsure 210–260 practice product Provides high-quality directions, interactive learning, and cooperative study activities. “Implementing Cisco Network Security”, also known as 210-260 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 210-260 dumps exam questions answers are updated (310 Q&As) are verified by experts. The associated certifications of 210-260 dumps is CCNA Security. It is providing Cisco 210–260 most actual study material with 3 months free updates. So you don’t need to take any street for https://www.pass4itsure.com/210-260.html dumps exam. Because Pass4itsure here for you.
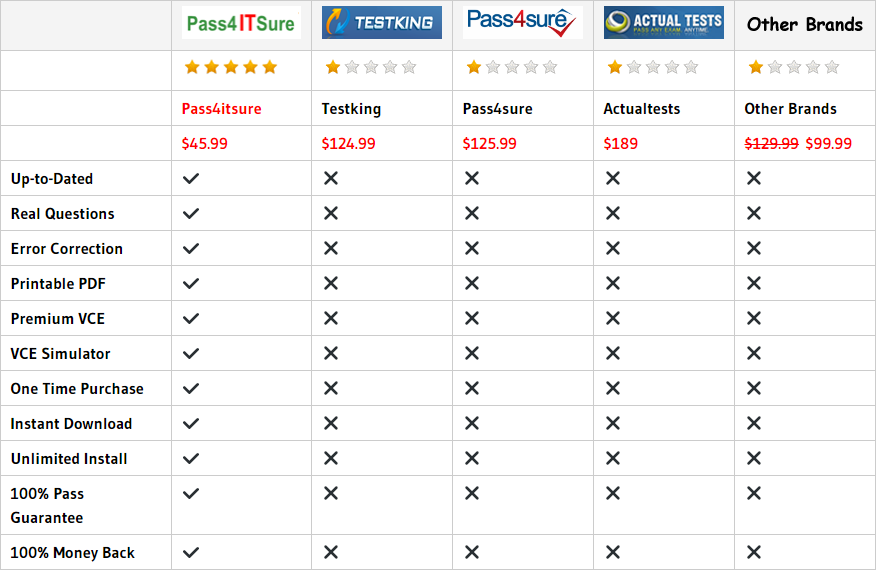
Compared with other brands, Pass4itsure has up to dated exam information, affordable price, instant exam PDF files downloaded, error correction, unlimited install,etc. Such as Pass4itsure 50% OFF Cisco 210-260 Dumps Exam Guide, Real Cisco 210-260 Dumps Demo Free Download Are Based On The Real Exam, We help you pass Implementing Cisco Network Security. Simple and Easy! To take advantage of the guarantee, simply contact Customer Support, requesting the exam you would like to claim. Pass4itsure guarantee insures your success otherwise get your MONEYBACK!