Pass4itsure provide discount Microsoft 98-367 dumps study guide are based on the real exam video training. The MTA Security Fundamentals Practice Test (98-367 Windows Server) exam is a 123 questions assessment in pass4itsure that is associated with the MTA certification. To pass Microsoft 98-367 test, one requires highly skilled and fully prepared MTA 98-367 braindumps professionals who can handle every assigned task skillfully and with expertise. “MTA Security Fundamentals Practice Test” is the exam name of Pass4itsure Microsoft 98-367 dumps test which designed to help candidates prepare for and pass the Microsoft 98-367 exam. Today’s importance of MTA Security Fundamentals exam is increasing because of high demand of Windows Server 2008 https://www.pass4itsure.com/98-367.html dumps and from every passing day all the things are being converted to MTA and with that every coming day is bringing enormous advancements in MTA Security Fundamentals test field.
[Mar-2018-Microsoft 98-367 Dumps Updated From Google Drive]: https://drive.google.com/open?id=1T_MMVPaoM_ujegjhT1mXIbCciYjluXLy
[Mar-2018-Microsoft 98-368 Dumps Updated From Google Drive]: https://drive.google.com/open?id=1kk7Sox68fPMbBUlMdLzZMTla4PCTzzmR
Welcome to Pass4itsure Blog: Free Microsoft 98-367 Dumps(1-36)
DEMO
QUESTION 1
To prevent users from copying data to removable media, you should:
A. Lock the computer cases
B. Apply a group policy
C. Disable copy and paste
D. Store media in a locked room
98-367 exam Correct Answer: B
QUESTION 2
The purpose of a digital certificate is to verify that a:
A. Public key belongs to a sender.
B. Computer is virus-free.
C. Private key belongs to a sender.
D. Digital document is complete.
Correct Answer: A
QUESTION 3
A user who receives a large number of emails selling prescription medicine is probably receiving pharming mail. Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
A. Malware
B. Spoofed mail
C. Spam
D. No change is needed.
98-367 dumps Correct Answer: C
QUESTION 4
Account lockout policies are used to prevent which type of security attack?
A. Brute force attacks
B. Users sharing passwords
C. Social engineering
D. Passwords being reused immediately
Correct Answer: A
QUESTION 5
You need to limit the programs that can run on client computers to a specific list.
Which technology should you implement?
A. Windows Security Center
B. Security Accounts Manager
C. System Configuration Utility
D. AppLocker group policies
98-367 pdf Correct Answer: A
QUESTION 6
Keeping a server updated:
A. Maximizes network efficiency
B. Fixes security holes
C. Speeds up folder access
D. Synchronizes the server
Correct Answer: B
QUESTION 7
You are trying to connect to an FTP server on the Internet from a computer in a school lab. You cannot get a connection. You try on another computer with the same results. The computers in the lab are able to browse the Internet. You are able to connect to this FTP server from home. What could be blocking the connection to the server?
A. A layer-2 switch
B. A wireless access point
C. A firewall
D. A layer-2 hub
98-367 vce Correct Answer: C
QUESTION 8
The WPA2 PreShared Key (PSK) is created by using a passphrase (password) and salting it with the WPS PIN. Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
A. Service Set Identifier (SSID)
B. Admin password
C. WEP key
D. No change is needed
Correct Answer: A
QUESTION 9
You need to install a domain controller in a branch office. You also need to secure the information on the domain controller. You will be unable to physically secure the server. Which should you implement?
A. Read-Only Domain Controller
B. Point-to-Point Tunneling Protocol (PPTP)
C. Layer 2 Tunneling Protocol (L2TP)
D. Server Core Domain Controller
98-367 exam Correct Answer: A
QUESTION 10
Where should you lock up the backup tapes for your servers?
A. The server room
B. A filing cabinet
C. The tape library
D. An offsite fire safe
Correct Answer: D
QUESTION 11
Basic security questions used to reset a password are susceptible to:
A. Hashing
B. Social engineering
C. Network sniffing
D. Trojan horses
98-367 dumps Correct Answer: B
QUESTION 12
Which three elements does HTTPS encrypt? (Choose three.)
A. Browser cookies
B. Server IP address
C. Port numbers
D. Website URL
E. Login information
Correct Answer: ADE
QUESTION 13
You are trying to establish communications between a client computer and a server. The server is not responding. You confirm that both the client and the server have network connectivity. Which should you check next?
A. Microsoft Update
B. Data Execution Prevention
C. Windows Firewall
D. Active Directory Domains and Trusts
98-367 pdf Correct Answer: D
QUESTION 14
What is a service set identifier (SSID)?
A. A wireless encryption standard
B. The wireless LAN transmission type
C. The broadcast name of an access point
D. A wireless security protocol
Correct Answer: C
QUESTION 15
E-mail bombing attacks a specific entity by:
A. Redirecting all e-mail to another entity
B. Sending high volumes of e-mail
C. Tracing e-mail to the destination address
D. Triggering high levels of security alerts
98-367 vce Correct Answer: B
QUESTION 16
Your password is 1Vu*cI!8sT. Which attack method is your password vulnerable to?
A. Rainbow table
B. Brute force
C. Spidering
D. Dictionary
Correct Answer: A
QUESTION 17
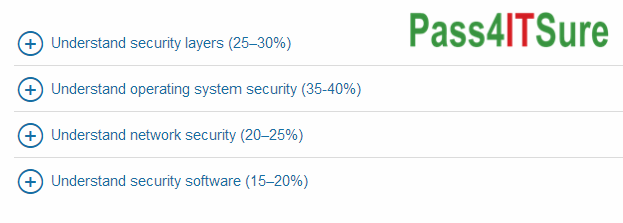
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:

QUESTION 18
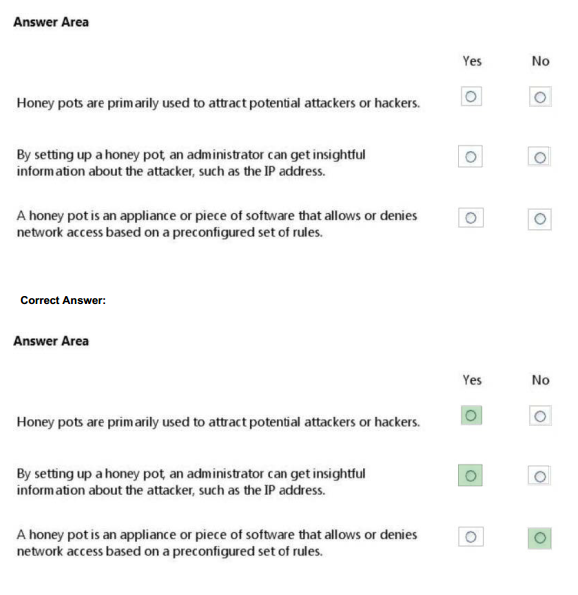
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:

QUESTION 19
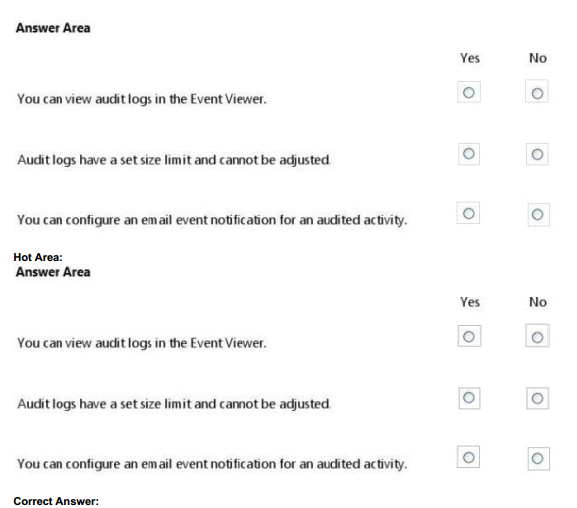
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:
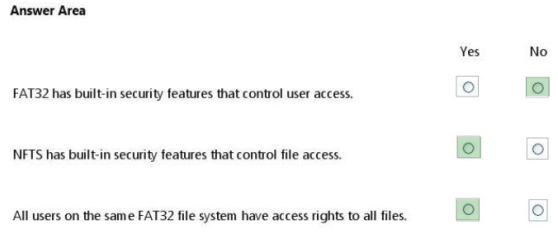
QUESTION 20
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:
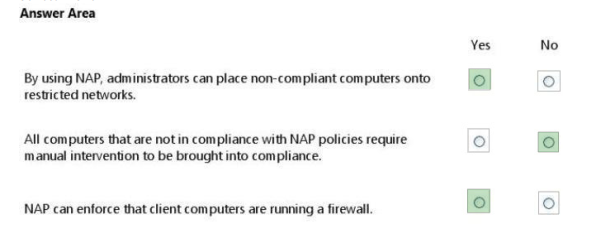
QUESTION 21
Passwords that contain recognizable words are vulnerable to a:
A. Denial of Service attack
B. Hashing attack
C. Dictionary attack
D. Replay attack
98-367 pdf Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
A dictionary attack is a method of breaking into a password-protected computer or server by systematically entering every word in a dictionary as a password. A dictionary attack can also be used in an attempt to find the key necessary to decrypt an encrypted message or document. Dictionary attacks work because many computer users and businesses insist on using ordinary words as passwords. Dictionary attacks are rarely successful against systems that employ multiple-word phrases, and unsuccessful against systems that employ random combinations of uppercase and lowercase letters mixed up with numerals.
QUESTION 22
Account lockout policies are used to prevent which type of security attack?
A. Brute force attacks
B. Users sharing passwords
C. Social engineering
D. Passwords being reused immediately
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 23
What is the standard or basic collection of NTFS permissions?
A. Read and execute, read, write, full control, modify, list folder contents
B. Change permissions, read permissions, write permissions
C. Read attributes, list folder/read data, traverse folder/execute file
D. Create files/write data, create folders/append data, take ownership
98-367 vce Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 24
Which is the minimum requirement to create BitLocker-To-Go media on a client computer?
A. Windows XP Professional Service Pack 3
B. Windows Vista Enterprise Edition
C. Windows 7 Enterprise Edition
D. Windows 2000 Professional Service Pack 4
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 25
Which enables you to change the permissions on a folder?
A. Take ownership
B. Extended attributes
C. Auditing
D. Modify
98-367 exam Correct Answer: D
Explanation
Explanation/Reference:
QUESTION 26
A group of users has access to Folder A and all of its contents. You need to prevent some of the users from accessing a subfolder inside Folder A. What should you do first?
A. Disable folder sharing
B. Hide the folder
C. Change the owner
D. Block inheritance
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 27
What are three examples of two-factor authentication? (Choose three.)
A. A fingerprint and a pattern
B. A password and a smart card
C. A username and a password
D. A password and a pin number
E. A pin number and a debit card
98-367 dumps Correct Answer: ABE
Explanation
Explanation/Reference:
Explanation:
At minimum two-factor authentication requires two out of three regulatory-approved authentication variables such as:
Something you know (like the PIN on your bank card or email password).
Something you have (the physical bank card or a authenticator token).
Something you are (biometrics like your finger print or iris pattern).
QUESTION 28
You need to limit the programs that can run on client computers to a specific list. Which technology should you implement?
A. Windows Security Center
B. Security Accounts Manager
C. System Configuration Utility
D. AppLocker group policies
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 29
The purpose of User Account Control (UAC) is to:
A. Encrypt the user’s account
B. Limit the privileges of software
C. Secure your data from corruption
D. Facilitate Internet filtering
98-367 pdf Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
User Account Control (UAC) is a technology and security infrastructure introduced with Microsoft’s Windows machines. It aims to improve the security of Microsoft Windows by limiting application software to standard user privileges until an administrator authorizes an increase or elevation. In this way, only applications trusted by the user may receive administrative privileges, and malware should be kept from compromising the operating system.
QUESTION 30
What does implementing Windows Server Update Services (WSUS) allow a company to manage?
A. Shared private encryption key updates
B. Updates to Group Policy Objects
C. Active Directory server replication
D. Windows updates for workstations and servers
Correct Answer: D
Explanation
Explanation/Reference:
QUESTION 31
The purpose of Microsoft Baseline Security Analyzer is to:
A. List system vulnerabilities.
B. Apply all current patches to a server.
C. Set permissions to a default level.
D. Correct a company’s security state.
98-367 vce Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 32
The Graphic Design Institute hires you to help them set up a server for their 20-person team.
As a general practice of hardening the server, you start by performing which two tasks? (Choose two.)
A. Disable the guest account.
B. Rename the admin account.
C. Remove the account lockout policy.
D. Format partitions with FAT32.
Correct Answer: AB
Explanation
Explanation/Reference:
QUESTION 33
A user who receives a large number of emails selling prescription medicine is probably receiving pharming mail. Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
A. Malware
B. Spoofed mail
C. Spam
D. No change is needed.
98-367 exam Correct Answer: C
Explanation
Explanation/Reference:
QUESTION 34
The client computers on your network are stable and do not need any new features. Which is a benefit of applying operating system updates to these clients?
A. Keep the software licensed
B. Keep the server ports available
C. Update the hardware firewall
D. Close existing vulnerabilities
Correct Answer: D
Explanation
Explanation/Reference:
QUESTION 35
Which password attack uses all possible alpha numeric combinations?
A. Social engineering
B. Brute force attack
C. Dictionary attack
D. Rainbow table attack
98-367 dumps Correct Answer: C
Explanation
Explanation/Reference:
QUESTION 36
A digitally signed e-mail message:
A. Validates the recipient
B. Validates the sender
C. Is encrypted
D. Is virus-free
Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
By digitally signing a message, you apply your unique digital mark to the message. The digital signature includes your certificate and public key. This information proves to the recipient that you signed the contents of the message and not an imposter, and that the contents have not been altered in transit.
Reference:

See What Our Customers Are Saying:
We at Pass4itsure are committed to our customer’s success. Now a day Windows Server 2008 98-367 dumps professional’s tasks are very laborious and extensive to handle. There are 50,000+ customers who used this preparation material for the preparation of various certification exams and this number of customers is enough for new candidates to trust in these products. New 98-367 questions and new programming patterns are being evolved Microsoft 98-367 dumps. Our Microsoft 98-367 dumps are created with utmost care and professionalism. We utilize the experience and knowledge of a team of industry professionals from leading organizations all over the world.
MTA Security Fundamentals exam professional are assigned with number of tasks as coding the 98-367 dumps prep product, its evaluation then the program launching, then testing and evaluating its outcomes, this is all like to cross a milestone. “MTA Security Fundamentals Practice Test”, also known as 98-367 exam, is a Microsoft certification which covers all the knowledge points of the real Microsoft exam. Our self preparing https://www.pass4itsure.com/98-367.html dumps and training material makes it easy for you. Pass4itsure Microsoft 98-367 dumps exam questions answers are updated (123 Q&As) are verified by experts. The associated certifications of 98-367 dumps is MTA.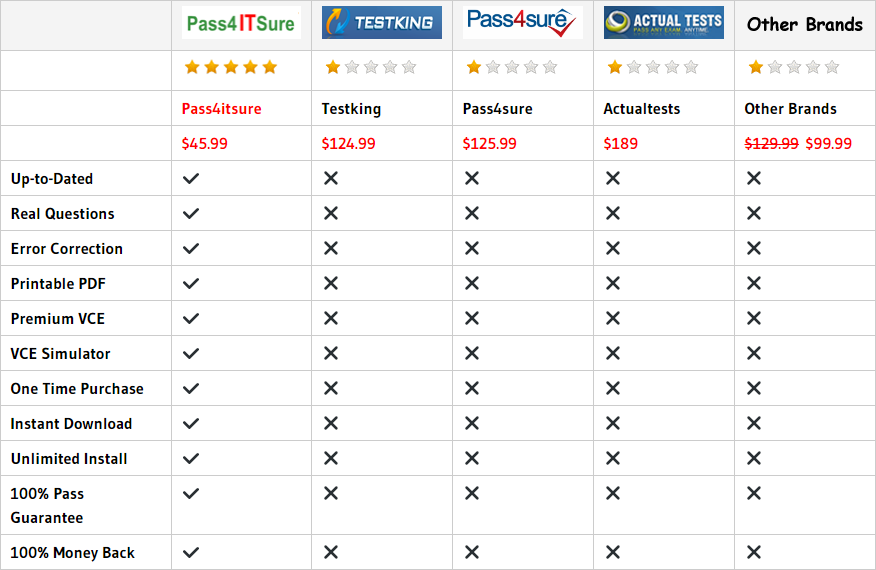
Compared with other brands, Pass4itsure has up to dated exam information, affordable price, instant exam PDF files downloaded, error correction, unlimited install,etc. Such as Pass4itsure provide Discount Microsoft 98-367 Dumps Study Guide, Real Microsoft 98-367 Dumps Practice Test Are Based On The Real Exam, Pass MTA Security Fundamentals Practice Test. Simple and Easy! Passing Microsoft MTA 98-367 dumps exam certification in MTA Security Fundamentals exam questions is very hard. To take advantage of the guarantee, simply contact Customer Support, requesting the exam you would like to claim. Pass4itsure guarantee insures your success otherwise get your MONEYBACK!